Contribute to help us improve!
Are there edge cases or problems that we didn't consider? Is there a technical pitfall that we should add? Did we miss a comma in a sentence?
If you have any input for us, we would love to hear from you and appreciate every contribution. Our goal is to learn from projects for projects such that nobody has to reinvent the wheel.
Let's collect our experiences together to make room to explore the novel!
To contribute click on Contribute to this page on the toolbar.
Authorization
-
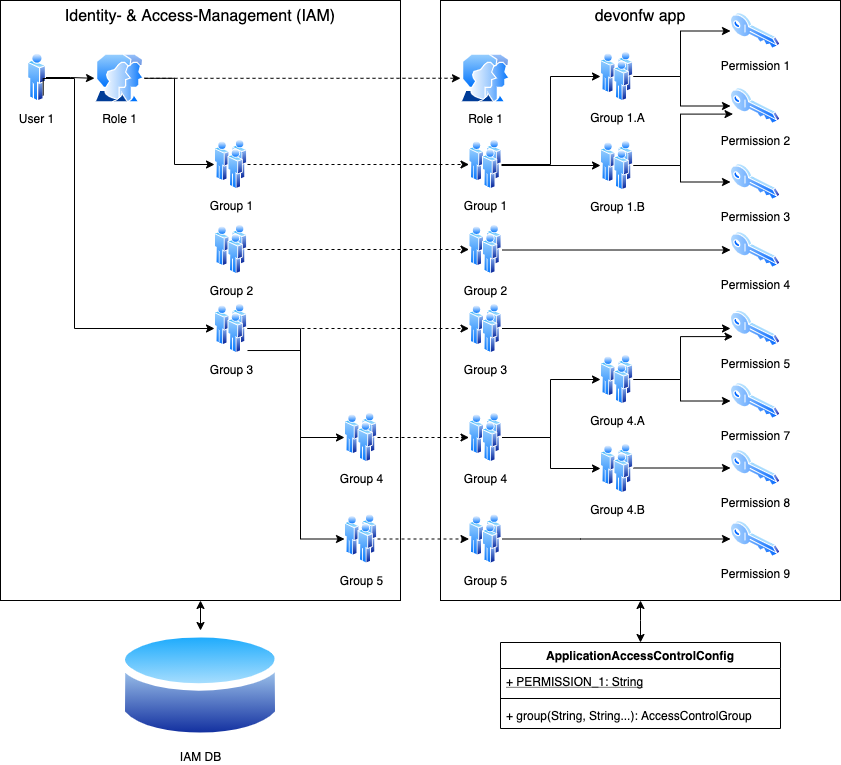
The Identity- and Access-Management is provided by according products and typically already available in the enterprise landscape (e.g. an active directory). It provides a hierarchy of primary access control objects (roles and groups) of a user. An administrator can grant and revoke permissions (indirectly) via this way.
-
The application security defines a hierarchy of secondary access control objects (groups and permissions). This is done by configuration owned by the application (see following section). The "API" is defined by the IDs of the primary access control objects that will be referenced from the Identity- and Access-Management.
Clarification of terms
| Term | Meaning and comment |
|---|---|
Authorization |
Verification that an authenticated user is allowed to perform the operation he intends to invoke |
Permission |
|
Group |
|
Role |
|
Access Control |
Any permission, group, role, etc., which declares a control for access management. |
Suggestions on the access model
For the access model we give the following suggestions:
-
Each Access Control (permission, group, role, …) is uniquely identified by a human readable string.
-
A unique permission is created for each use-case.
-
Groups combine permissions to typical and useful sets for the users.
-
Roles act as specific groups as required by our business demands.
-
Users can be associated with a list of Access Controls.
-
For authorization of an implemented use case the required permissions are determined. A security exception is thrown if the user does not have the required permissions.
-
A user has no permission by default and only those granted to him explicitly give him additional permission for specific things. Permissions granted can not be reduced by other permissions.
-
Permissions are secrets of the application. Administrators shall not fiddle with individual permissions but grant them via groups. So the access management provides a list of strings identifying the Access Controls of a user. The individual application itself contains these Access Controls in a structured way, whereas each group forms a permission tree.
Naming conventions
As stated above each Access Control is uniquely identified by a human readable string. This string should follow the naming convention:
«app-id».«local-name»For Access Control Permissions the «local-name» again follows the convention:
«verb»«object»The segments are defined by the following table:
| Segment | Description | Example |
|---|---|---|
«app-id» |
Is a unique technical but human readable string of the application (or microservice).
It shall not contain special characters and especially no dot or whitespace.
We recommend to use |
|
«verb» |
The action that is to be performed on «object».
|
|
«object» |
The affected object or entity. Shall be named according to your data-model |
|
So as an example shop.FindProduct will reflect the permission to search and retrieve a Product in the shop application.
The group shop.ReadMasterData may combine all permissions to read master-data from the shop.
However, also a group shop.Admin may exist for the Admin role of the shop application.
Here the «local-name» is Admin that does not follow the «verb»«object» schema.